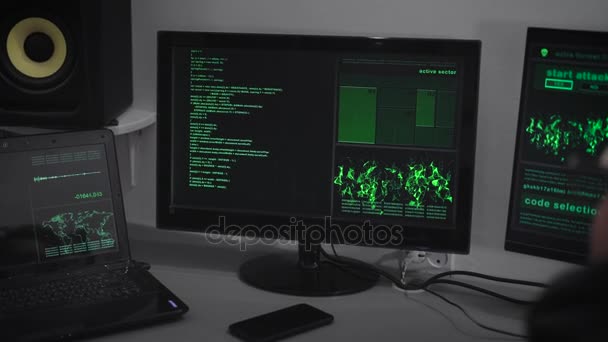
Dangerous Hacker Braking and Getting Access into Government Data — Photo
L
2000 × 1125JPG6.67 × 3.75" • 300 dpiStandard License
XL
5000 × 2813JPG16.67 × 9.38" • 300 dpiStandard License
super
10000 × 5626JPG33.33 × 18.75" • 300 dpiStandard License
EL
5000 × 2813JPG16.67 × 9.38" • 300 dpiExtended License
Dangerous Hacker Braking and Getting Access into Government Data Centre.
— Photo by Gorodenkoff- AuthorGorodenkoff

- 163523788
- Find Similar Images
- 5
Stock Image Keywords:
- cyber
- information
- exploit
- spy
- malicious
- monitor
- hacking
- technology
- attack
- display
- teal
- government
- internet
- malware
- code
- system
- leak
- surveillance
- programming
- dark
- jacking
- cryptocurrency
- email
- virus
- hacker
- deep
- interface
- screen
- security
- infect
- company
- vulnerability
- cybercrime
- revolution
- anonymous
- election
- room
- web
- identity
- phishing
- software
- server
- privacy
- data
- Crypto
- executing
- corporate
- access
- computer
Same Series:
















Same Model:
















Similar Stock Videos:














Usage Information
You can use this royalty-free photo "Dangerous Hacker Braking and Getting Access into Government Data" for personal and commercial purposes according to the Standard or Extended License. The Standard License covers most use cases, including advertising, UI designs, and product packaging, and allows up to 500,000 print copies. The Extended License permits all use cases under the Standard License with unlimited print rights and allows you to use the downloaded stock images for merchandise, product resale, or free distribution.
You can buy this stock photo and download it in high resolution up to 5000x2813. Upload Date: Aug 16, 2017
