Cyber security background Stock Photos
100,000 Cyber security background pictures are available under a royalty-free license
- Best Match
- Fresh
- Popular
























































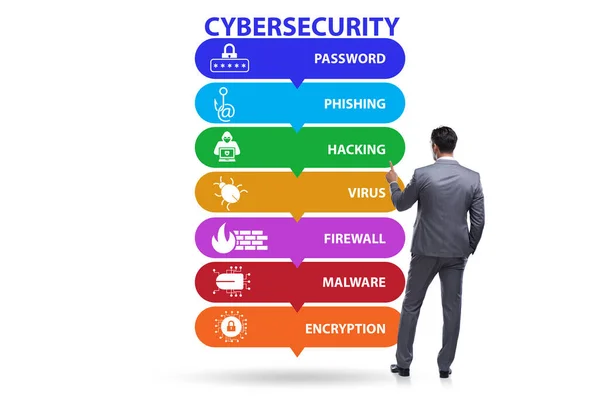












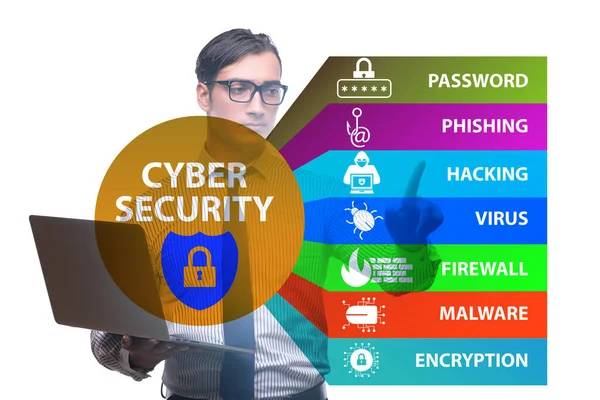




























Related image searches
Discover the Perfect Cyber Security Background Images for Your Projects
In today's digital era, where the importance of cyber security cannot be overstated, it's crucial to convey the right message through your visuals. Whether you're working on a presentation, website, or any other project related to cyber security, choosing the right background images is essential. That's why we offer a vast collection of stock images that are not only visually captivating but also highly relevant to the topic. In this article, we will explore our selection of cyber security background images, the file formats available, and provide practical tips on how to effectively use them for various projects.
Wide Range of Cyber Security Background Images
Our stock image library boasts a wide range of cyber security background images, suitable for all your design needs. From futuristic technology concepts to abstract representations of online protection, we offer images that cater to every aspect of cyber security. Discover stunning visuals of interconnected networks, high-tech security systems, and mysterious coded backgrounds. These images are curated by experts in the field to ensure they evoke the right emotions and convey the professionalism and seriousness associated with cyber security.
Additionally, our collection includes images related to encryption, data privacy, and network security. These visuals are perfect for illustrating the complex concepts and challenges involved in safeguarding sensitive information. Choose from a variety of styles, colors, and compositions to find the image that best aligns with your project's mood and message. Remember, the right image can instantly captivate your audience and make a lasting impact.
Supported File Formats and Their Appropriate Usage
We provide images in three widely-used file formats: JPG, AI, and EPS. Each format has its unique advantages and recommended usage.
JPG (Joint Photographic Experts Group) files are the most common and widely supported format. They are ideal for web-based projects such as websites, blogs, and social media posts. Their compressed file size allows for faster loading times without compromising image quality. When using JPG images, ensure they are of high resolution to maintain clarity and avoid pixelation.
For projects requiring scalability and flexibility, AI (Adobe Illustrator) files are recommended. These vector-based images can be resized indefinitely without losing quality, making them ideal for print materials like brochures, posters, and business cards. When utilizing AI files, ensure you have the necessary software, such as Adobe Illustrator, to open and modify them.
EPS (Encapsulated PostScript) files are another vector-based format suitable for print materials. They offer similar advantages as AI files, particularly when working on large format designs like billboards or banners. EPS files can be easily resized and manipulated to fit any size requirement without sacrificing image quality. Most professional design software, such as Adobe Photoshop and CorelDRAW, support EPS files.
Expert Advice for Using Cyber Security Background Images
When incorporating cyber security background images into your projects, keep these expert tips in mind:
1. Align with your message: Choose images that align with the specific message you're trying to convey. For example, if you're emphasizing the importance of data encryption, select an image that visually represents encryption algorithms or lock icons.
2. Consider your audience: Understand your target audience and use images that resonate with them. Tailor your choices based on their level of technical expertise and preferences.
3. Balance professionalism and creativity: Cyber security projects require a balance between professionalism and creativity. Select images that showcase your expertise while adding a touch of innovation and visual appeal.
4. Adapt to the project's tone: Cyber security can convey a range of tones, from serious and corporate to futuristic and cutting-edge. Ensure your chosen images align with the overall tone of your project to create a cohesive visual experience.
By following these guidelines, you can effectively leverage our cyber security background images to enhance the impact and effectiveness of your projects. Remember, visuals can be powerful tools in communicating complex concepts and conveying the importance of cyber security.
So, explore our extensive library, choose the perfect cyber security background images in the right format, and let your designs speak volumes about your dedication to protecting sensitive information and staying ahead in the digital world.